Category: Uncategorized
Companies Face Massive Biometric Information Privacy Act (BIPA) Allegations with Virtual Try-On Technology
Virtual try-on technology (“VTOT”) allows consumers to use augmented reality (“AR”) to see what a retailer’s product may look like on their body. By providing the retailer’s website access to their device’s camera, consumers can shop and try on products from the comfort of their home without ever stepping into a brick-and-mortar storefront. Retailers provide customers the option to virtual-try consumer goods through their website, app, or through social media filters like Instagram, Snapchat, and TikTok. While virtual try-on emerged in the early 2010s, the COVID-19 pandemic spurred its growth and adoption amongst consumers. Retailers, however, have seen a recent uptick in lawsuits due to biometric privacy concerns of virtual-try on technology, especially in Illinois. In 2008, Illinois passed the Biometric Information Privacy Act (“BIPA”), one of the strongest and comprehensive biometric privacy acts in the country.
This blog post will explore current lawsuits in Illinois and the Seventh Circuit that could impact how retailers and consumers use virtual-try on technology, as well as the privacy and risk implications of the technology for both groups.
Background on Virtual Try-On
From trying on eyeglasses to shoes, virtual try-on technology allows consumers an immersive and fun opportunity to shop and visualize themselves with a product without ever leaving their homes. Fashion brands often use virtual try-on technology to enhance consumer experiences and find that it may positively affect purchase decisions and sales. By providing customers with the opportunity to shop from home, customers may be less likely to return the item, since they are more likely to pick the correct product the first time through the enhanced virtual-try on experience. With revenue in the AR and VR market expected to exceed $31 billion dollars in 2023 and one-third of AR users having used the technology to shop, brands are responding to the growing demand for AR and virtual try-on.
Although the pandemic really drove brands to grow their virtual try-on and AR offerings, brands have used virtual try-on for many years prior. Sephora launched an augmented reality mirror back in 2014. Maybelline allowed consumers to virtually try on nail polish. In the summer of 2019, L’Oreal Group partnered with Amazon to integrate ModiFace, the company’s AR and artificial intelligence (“AI”) company, into Amazon’s marketplace. The pandemic only pushed brands to grow those offerings.
By mid-2021, social media and tech brands expanded their AR offerings to cash in on the increasing role that virtual try-on has on consumers’ purchase decisions. Perfect Corp., a beauty technology company, integrated with Facebook in 2021 to expand the platform’s AR offerings specifically geared towards beauty. The integration allows Facebook to make it easier and cheaper for brands and advertisers to “integrate their catalogs with AR.” The integration expanded who could use Meta’s platforms for AR-enhanced shopping since any merchant who uses Perfect Corp. could advantage of Facebook’s Catalog, AR-enabled advertisements, and Instagram Shops. Perfect Corp.’s CEO Alice Chang wrote in the announcement:
“There’s no denying the impact that social media platforms like Instagram continue to play in the consumer discovery and shopping journey. This integration underlines the importance of a streamlined beauty shopping experience, with interactive AR beauty tech proven to drive conversion and enhance the overall consumer experience.”
That same week, Facebook, now Meta, announced their integration with Perfect Corp. and later announced plans to integrate ModiFace into its new advertising formats. In addition, Meta’s Instagram also partnered with L’Oréal’s ModiFace. With the swipe of a button, consumers on Instagram can try on new lipsticks and then purchase the product immediately within the app. The expansion of AR features on Meta’s platforms makes it seamless for consumers to shop not only without leaving their home and without leaving the app.
Outside of Meta, Snapchat offers consumers the chance to use various lenses and filters, including the AR shopping experiences. In 2022, Nike sponsored its own Snapchat lens to allow consumers to try on and customize their own virtual pair of Air Force 1 sneakers. Consumers could swipe through several colors and textures. Once satisfied, consumers could then select “shop now” to purchase their custom Nike Air Force 1s instantaneously.
Rising Biometric Concerns and Lawsuits
While demand for AR and virtual try-on is growing, the innovative technology does not come without major concerns. Brands like Charlotte Tilbury, Louis Vuitton, Estee Lauder, and Christian Dior have been slapped with class actions lawsuits in Illinois and the Seventh Circuit for violating BIPA.
According to the American Civil Liberties Union (“ACLU”) of Illinois, BIPA requires that private companies: (1) inform the consumer in writing of the data they are collecting and storing, (2) inform the consumer in writing regarding the specific purpose and length of time that the data will be collected, stored, and used, and obtain written consent from the consumer. Additionally, BIPA prohibits companies from selling or profiting from consumer biometric information. The Illinois law is considered to be one of the most stringent biometric privacy laws in the country and stands to be one of the only laws of its kind “to offer consumers protection by allowing them to take a company who violates the law to court.” BIPA allows consumers to recover up to $1,000 of liquidated damages or actual damages per violation, whichever is greater, in addition to attorneys’ fees and expert witness fees.
In November 2022, an Illinois federal judge allowed a BIPA lawsuit to move forward against Estee Lauder Companies, Inc. in regards to their Too Faced makeup brand. The plaintiff alleges that the company collected her facial-geometry data in violation of BIPA when she used the makeup try-on tool available on Too Faced’s website. Under Illinois law, a “violation of a statutory standard of care is prima facie evidence of negligence.” Kukovec v. Estee Lauder Companies, Inc., No. 22 CV 1988, 2022 WL 16744196, at *8 (N.D. Ill. Nov. 7, 2022) (citing Cuyler v. United States, 362 F.3d 949, 952 (7th Cir. 2004)). While the judge ruled that the plaintiff did not sufficiently allege recklessness or intent, he allowed the case to move forward because the plaintiff “present[ed] a story that holds together,” and did more than “simply parrot the elements of a BIPA claim.” The judge found that it seemed reasonable to infer that the company had to collect biometric data for the virtual try-on to work.
In February 2023, Christian Dior was able to find a BIPA exemption, which allowed a class action lawsuit filed against them to be dismissed. Christian Dior offered virtual try-on for sunglasses on their website. According to the lead plaintiff, the luxury brand failed to obtain consent prior to capturing her biometric information for the virtual-try on offering violating BIPA. The judge, however, held that the BIPA general health care exemption applied to VTOT for eyewear, including nonprescription sunglasses offered by consumer brands. BIPA exempts information captured from a “patient” in a “health care setting.” Since BIPA does not define these terms, the judge referred to Merriam-Webster to define the terms. Patient was defined as “an individual awaiting or under medical care and treatment” or “the recipient of any various personal services.” The judge found sunglasses, even nonprescription ones, are used to “protect one’s eyes from the sun and are Class I medical devices under the Food & Drug Administration’s regulations.” Thus, an individual using VTOT is classified as a patient “awaiting . . . medical care” since sunglasses are a medical device that protect vision and VTOT is the “online equivalent” of a brick-and-mortar store where one would purchase sunglasses.
Further, health care was defined as “efforts made to maintain or restore physical, mental, or emotional well-being especially by trained and licensed professionals.” The judge stated that she had “no trouble finding that VTOT counts as a ‘setting.’” Thus, under BIPA’s general health care exemption, consumers who purchase eyewear, including nonprescription sunglasses, using VTOT are considered to be “patients” in a “health care setting.”
Both cases show that while virtual try-on may operate similarly on a company’s website, the type of product that a brand is offering consumers the opportunity to “try on” may allow them to take part in exemptions. The “health care” exemption in the Christian Dior was not the first time that a company benefitted from the exemption. BIPA lawsuits can be costly for companies. TikTok settled a $92 million BIPA lawsuit in 2021 with regards to allegations that the social media app harvested biometric face and voice prints from user-uploaded videos. Although that example does not deal with virtual try-on, it exemplifies how diligence and expertise with BIPA requirements can save brands huge settlements. Companies looking to expand into the virtual try-on space should carefully consider how they will obtain explicit written consent (and other BIPA requirements, like data destruction policies and procedures) from consumers to minimize class action and litigation exposure.
INTRODUCTION
We live in an insatiable society. Across the globe, particularly in the United States, everyone with an Instagram account knows that the “phone eats first.” Young professionals rush to happy hour to post the obligatory cocktail cheers video before they take their first sip. On Friday nights, couples sprint to their favorite spot or the up-and-coming Mediterranean restaurant to quickly snap a picture of the “trio of spreads.” Everyone from kids to grandparents alike are flocking to the nearest Crumbl every Monday to share a picture of the pink box and the half-pound cookie inside. Social media has created a food frenzy. We are more obsessed with posting the picture of a meal than eating the meal itself. While a psychologist might have a negative view of the connection between social media and food, the baker or chef behind the photogenic creation is ecstatic by the way platforms such as Instagram and YouTube bring new patrons into their storefronts.
Due to the rise of social media over the past twenty years, food has become an obsession in our society. Many of us are self-proclaimed “foodies.” Historically, food has not fit neatly into the intellectual property legal scheme in the United States. Trademark, trade dress, and trade secrets are often associated with food, but we rarely see recipes or creative platings receive patent or copyright protection. Intellectual property law is not as enthralled with food as many of us are, but pairing the law with social media may create another way to protect food.
A RECIPE FOR IP PROTECTION
There are four main types of intellectual property: patents, copyrights, trade secrets, and trademarks. The utilitarian and economic perspectives are the two main theories behind intellectual property law. The utilitarian purpose of food is to be consumed. Economically, the food business in America is a trillion-billion-dollar industry. Intellectual property law aims to promote innovation, creativity, and economic growth. All three of these goals can be found within the food industry; however, the recipe for intellectual property protection has yet to be perfected.
Patent law is designed to incentivize and promote useful creations and scientific discoveries. Patent law gives an inventor the right to exclude others from using the invention during the patent’s term of protection. To qualify for a patent, an invention must be useful, novel, nonobvious, properly disclosed, and made up of patentable subject matter. Patentable subject matter includes processes, machines, manufactures, compositions of matter, and improvements thereof. Novelty essentially requires that the patent be new. It is a technical and precise requirement that often creates the biggest issue for inventors. Novelty in the context of food “means that the recipe or food product must be new in the sense that it represents a previously unknown combination of ingredients or variation on a known recipe.” According to the U.S. Court of Customs and Patent Appeals, to claim protection in food products, “an applicant must establish a coaction or cooperative relationship between the selected ingredients which produces a new, unexpected, and useful function.”A person cannot simply add or eliminate common ingredients, treating them in ways that would differ from the former practice. There are very few patents for food, but common examples include Cold Stone Creamery’s signature Strawberry Passion ice cream cake and Breyer’s Viennetta ice cream cake.
Copyright law affords protection to creative works of authorship that are original and fixed in a tangible medium. Fixation is met “when its embodiment … is sufficiently permanent or stable to permit it to be perceived, reproduced, or otherwise communicated for a period of more than transitory duration.” The Supreme Court has stated, “that originality requires independent creation plus a modicum of creativity.” Copyrights are not extended to “any idea, procedure, process, system, method of operation, concept, principle, or discovery.” Food, specifically food designs, are typically not eligible “for copyright protection because they do not satisfy the Copyright Act’s requirement that the work be fixed in a tangible medium.” A chef does not acquire rights for being the first to develop a new style of food because this creation is seen as merely ideas, facts, or formulas. Furthermore, shortly after a food’s creation, it is normally eaten, losing its tangible form. Recipes alone are rarely given copyright protection because recipes are considered statements of facts, but “recipes containing other original expression, such as commentary or artistic elements, could qualify for protection.”
Trade secrets are more favorable to the food industry. Traditionally, trade secret law has encompassed recipes. To be a trade secret the information must be sufficiently secret so that the owner derives actual or potential economic value because it is not generally known or readily ascertainable. The owner must make reasonable efforts to maintain the secrecy of the information. It is unlikely that food design, the shape and appearance of food, will be given trade secret protection as “food design presents a formidable challenge to trade secret protection: once the food is displayed and distributed to consumers, its design is no longer secret.” However, certain recipes, formulas, and manufacturing and preparation processes may be protected by trade secret law. Regarding food and intellectual property, trade secrets are probably the most well-known form of IP. Examples of still valid trade secret recipes and formulas include Coca-Cola’s soda formula, the original recipe for Kentucky Fried Chicken, the recipe for Twinkies, and the recipe for Krispy Kreme donuts.
Trademark is the most favorable type of IP protection given to the food industry. Trademarks identify and distinguish the source of goods or services. Trademarks typically take the form of a word, phrase, symbol, or design. Trade dress is a type of trademark that refers to the product’s appearance, design, or packaging. Trade dress analyzes “the total image of a product and may include features such as size, shape, color or color combinations, texture, graphics, or even particular sales techniques.”
Different types of trademarks and trade dress receive different levels of protection. For trademarks, it depends on the kind of mark. Courts determine whether the mark is an inherently distinctive mark, a descriptive mark, or a generic mark. Similarly, trade dress receives different levels of protection depending on whether the trade dress consists of product packaging or product design. In the context of food, ‘the non-functionality of a particular design or packaging is required” for a product to receive protection as trade dress. Some examples of commonly-known trademarks include Cheerios, the stylized emblematic “M” logo from McDonald’s, and the tagline “Life tastes better with KFC.” Food designs that have federally registered trademarks under trade dress include: Pepperidge Farm’s Milano Cookies, Carvel’s Fudgie the Whale Ice Cream Cake, Hershey’s Kisses, General Mills’ Bugles, Tootsie Rolls and Tootsie Pops, and Magnolia Bakery’s cupcakes bearing its signature swirl icing.
SOCIAL MEDIA – THE LAST DEFENSE
When it comes to food, there is no recipe to follow to receive intellectual property protection, but social media can be a way for bakers, chefs, and restauranteurs to be rewarded for their creations and ensure creativity in the food industry. Social media influences the way businesses conduct and plan their marketing strategies. Many businesses use social media to communicate with their audience and expand their consumer base. Social media allows a chef to post the week’s “Specials Menu” to their restaurant’s Instagram, and in a few seconds, anyone who follows that account can post that menu on their account and share it with hundreds if not thousands of people. As noted previously, this single menu would not receive IP protection because it is primarily fact-based, not a secret, is obvious, and is likely not a signifier of the restaurant to the general public. However, the power of social media will bring hundreds of excited and hungry foodies to the business.
Social media alone cannot ensure that another chef or baker won’t reverse engineer the dish featured on the special’s menu, but social media has done what IP cannot. The various social media platforms embody what the framers of the Constitution were trying to accomplish through intellectual property when they drafted Article I centuries ago — the promotion of innovation, creativity, and economic growth. The Constitution states that “Congress shall have power to … promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries….” While there is no indication that the framers ever intended food to be a part of what they knew to be intellectual property, two hundred and fifty years later, it is clear that food is a mainstay in the IP world, even if it does not fit systematically into patents, copyrights, trademarks, or trade secrets. Unfortunately, the law has fallen short when addressing IP protection for the food industry; but, luckily social media has continued to fulfill the goal of intellectual property that the framers desired when it comes to the food industry.
Social media allows others to connect with the satisfying creation and gives chefs the opportunity to be compensated for their work. After seeing the correlation between the Instagram post and the influx of guests, the chef will be incentivized to create more. The chef will cook up another innovative menu for next week, hoping that she will receive the same positive reward again. The food industry is often left out, unable to fit into the scope of IP law, but through social media, chefs and bakers can promote innovation, creativity, and economic growth at the touch of their fingers.
Alessandra Fable is a second-year law student at Northwestern Pritzker School of Law.
Introduction
In April 2022, someone paid $130,000 for a pair of Nike Dunks. Here’s the kicker – it was for a pair of virtual sneakers. Shelling out five to six figures for a pair of exclusive shoes is not rare in the sneaker world, but paying that much for a pair of virtual kicks is unprecedented.
This sale illustrates Nike’s wider strategy in conquering the next frontier of commerce: the metaverse. In 2021, Nike started making strategic investments to grow and protect its brand in the metaverse. First, Nike submitted several trademark applications with the United States Patent and Trademark Office for virtual goods. Second, Nike announced a partnership with Roblox, an online gaming platform, to create a Nike-branded virtual world where gamers can play virtual games and dress their avatar in digital versions of Nike’s products. Third, Nike acquired RTFKT, an organization that creates unique digital sneakers. John Donahoe, Nike’s President and CEO, described the acquisition as “another step that accelerates Nike’s digital transformation and allows us to serve athletes and creators at the intersection of sport, creativity, gaming and culture.”
Nike is not the only brand exploring the metaverse. Other brands are now offering virtual merchandise through NFTs, including other sportswear brands like Asics and Adidas, luxury fashion brands like Hermès and Gucci, and even fast-food chains like Wendy’s and Taco Bell. Despite these companies’ growing activity in the space, the application of current intellectual property protection to branded NFTs is still unclear. A recent complaint filed by Nike against StockX, a popular sneaker resale platform, illustrates this uncertainty. The outcome of this case could determine the scope of trademark protection in the metaverse and will have serious implications on the commercial viability of brands’ significant investments in the space.
The Nike StockX Lawsuit
In February 2022, Nike sued StockX, a popular sneaker resale platform, after StockX began selling Nike-branded NFTs alongside physical Nike sneakers. The complaint, filed in the United States District Court for the Southern District of New York, laid out several causes of action, including trademark infringement. Nike stated that it “did not approve of or authorize StockX’s Nike-branded Vault NFTs. . . Those unsanctioned products are likely to confuse consumers, create a false association between those products and Nike, and dilute Nike’s famous trademarks.”
In its answer, StockX raises two key defenses. First, it claims that its “use of images of Nike sneakers and descriptions of re-sale Nike products in connection with StockX NFTs is nominative fair use. It is no different than major e-commerce retailers and marketplaces who use images and descriptions of products to sell physical sneakers and other goods, which consumers see (and are not confused by) every single day.” Second, StockX raises a first sale defense, arguing that “Nike’s claims are barred, in whole or in part, by the first sale doctrine permitting purchasers of lawfully trademarked goods to display, offer, and sell those good under their original trademark.” Thus, the outcome of the case turns on how courts will apply traditional intellectual property doctrines to more modern trademark issues.
StockX’s Nominative Fair Use Defense
Nominative fair use is an affirmative defense for defendants who use another’s trademark deliberately to refer to that party, for purposes such as advertising, commentary, and news reporting. To raise a successful nominative fair use defense, the user must meet three requirements: “First, the product or service in question must be one not readily identifiable without use of the trademark; second, only so much of the mark or marks may be used as is reasonably necessary to identify the product or service; and third, the user must do nothing that would, in conjunction with the mark, suggest sponsorship or endorsement by the trademark holder.”
StockX can likely meet the first and second requirements but will struggle to meet the third. StockX can argue that it would be difficult to sell the virtual NFT Nike sneaker without using Nike’s trademarked logo and that it is only using the Nike logo as much as reasonably necessary for the consumer to identify the product. As StockX’s argues in its answer, “the image and product name on the Vault NFT play a critical role in describing what goods are actually being bought and sold.” As some have pointed out, the Nike logo “does not appear to be used by StockX separate and apart from its appearance in the photo of the shoes corresponding to the NFT.”
At issue is the third requirement regarding an implied sponsorship or endorsement. StockX’s website includes a disclaimer of any affiliation with the Nike brand, but it is unclear if this adequately safeguards against consumer protection. Nike’s complaint characterizes the disclaimer as “comically and intentionally small” and “difficult to read.” As evidence that the disclaimer does not prevent consumer confusion, Nike points to numerous social media users who expressed uncertainty as to whether Nike endorses, approves, or gets a commission from StockX’s NFT sales. This confusion is further compounded by the fact that Nike sells its own NFTs. Thus, StockX will likely have difficulty in succeeding on its nominative fair use defense.
StockX’s First Sale Defense
The success of StockX’s first sale defense requires a more complex, fact-intensive analysis. The first sale defense establishes that “the right of a producer to control distribution of its trademarked product does not extend beyond the first sale of the product.” Whether or not this rule applies to Nike’s case, however, depends on how the court characterizes the NFT. On one hand, StockX will argue that its NFTs are each tied to the resale of a physical Nike shoe – similar to a receipt – and thus fall under the first sale doctrine. On the other hand, Nike will argue that the NFTs are standalone, separate products and thus are not protected by the first sale doctrine. To succeed on the trademark infringement claim, Nike must establish that the NFT and the physical shoe are two independent products.
On its website, StockX added a disclaimer in an attempt to address this issue directly, “Please note: the purpose of Vault NFT is solely to track the ownership and transactions in connection with the associated product. Vault NFTs do not have any intrinsic value beyond that of the underlying associated product” (emphasis added). However, this disclaimer does not preclude Nike from demonstrating that there is a separate value and that the shoe and the NFT are independent products.
First, Nike can point to the fact that the NFTs being sold on StockX are generally more expensive than the value of the sneaker itself (even if one accounts for the markup of sneakers that is common in the resale market). Nike points to this divergence in monetary value: “Thus far, StockX has sold Nike-branded Vault NFTs at prices many multiples above the price of the physical Nike shoe.” For example, as of October 25, 2022, the Nike Dunk Low Off-White Lot 50 was on sale for $715. The NFT of that very same shoe, however, was on sale for $8,500. This significant divergence in price suggests that there is an independent economic value of the NFT beyond the ownership of the physical shoe.
Second, Nike can argue that the NFTs are an independent product because NFT ownership gives consumers unique perks. When the program initially launched, StockX’s website explicitly stated that NFT “owners may also receive exclusive access to StockX releases, promotions, events, as a result of ownership.” Since the lawsuit, this language has been removed, likely because it could be used as ammunition by Nike to defeat the first sale defense. But NFT owners still get some exclusive perks. For example, the ownership of the NFT means that StockX will store the physical shoe in their “brand new, climate-controlled, high-security vault” and NFT owners will be able to flip/trade the shoe instantaneously, rather than waiting for the shoes to be shipped or paying shipping fees. The storage and the ability to bypass shipping costs associated with flipping sneakers are benefits that are unique to owners of the NFTs but are unavailable to those who only own the physical show.
Conclusion
The Nike-StockX litigation highlights the uncertainty of how traditional intellectual property law applies to more modern trademark issues. The outcome of the case will have serious implications for how companies can protect their brands in the growing world of virtual commerce.
Jeanne Boyd is a second-year JD student at the Northwestern Pritzker School of Law.
In January 2022, after nearly one hundred years of copyright protection, Winnie-the-Pooh entered the public domain. This blog post will discuss copyright law’s grounding in the Constitution, the story of Winnie-the-Pooh’s copyright, and how the changing landscape of U.S. copyright law has affected this beloved story and the characters contained within it.
Congress’ Power to Enact Federal Copyright Law
Congress’ power to regulate federal copyright law derives from the Constitution. Specifically, Article 1, Section 8, Clause 8 (the “Intellectual Property” Clause) grants Congress the power “[t]o promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.” While this clause grants Congress general powers to govern certain aspects of intellectual property law, it does not actually supply any laws on its own. Instead, acting pursuant to this constitutional authority, Congress can write and enact federal copyright laws.
Congress enacted its first set of federal copyright laws in the late 1700’s. The laws were relatively limited in scope, protecting “books, maps, and charts for only fourteen years with a renewal period of another fourteen years.” Modern copyright laws have since become more expansive, protecting a wider variety of works for longer periods of time.
The copyright laws relevant to Winnie-the-Pooh are: (1) the 1909 Copyright Act, (2) the 1976 Copyright Act, and (3) the 1998 Copyright Term Extension Act. Under all three Acts, an original work of authorship gains copyright protection the moment it is published. The copyright protection immediately grants the author exclusive rights to reproduce, distribute, perform, and display the work. Further, all three Acts permit authors to transfer these rights to third parties, which is often exercised by authors in exchange for royalty income. While these three copyright Acts are very similar in substance, their primary differences relate to the amount of time that authors enjoy these protections.
- The 1909 Act
Under this Act, works could receive protection for up to 56 years. Upon publication, a work was initially protected for 28 years, and if the copyright was renewed in its 28th year, an additional protection term of 28 years was granted.
- The 1976 Act
The 1976 Copyright Act made one significant change to the renewal term of works created before 1978; it gave all current copyrights an additional 20 years of protection, for a total of 76 years. Additionally, this Act gave authors an opportunity to terminate any licensing agreements previously made under the 1909 Act.
- The 1998 Copyright Term Extension Act
The 1998 Copyright Term Extension Act added yet another 20 years to the renewal period of previously copyrighted works, which automatically applied to works “subsisting in their second term between December 31, 1976, and December 31, 1977,” and extended the maximum length of copyright protection to 95 years.
Winnie-the-Pooh’s Copyright
In 1926, Alan Alexander Milne wrote Winnie-the-Pooh, the first of several collections of short stories about a boy named Christopher Robin, his stuffed bear, Winnie-the-Pooh, and their friends in the Hundred Acre Wood. Since the book was published during the 1909 Copyright Act regime, it automatically gained copyright protection upon publication through 1954, and received an additional 28 years of protection because the copyright was renewed. The 1976 Copyright Act further extended Winnie-the-Pooh’s protection through 2001, and the 1998 Copyright Term Extension Act tacked an additional 20 years of subsequent protection. Since the 1998 Act was the final extension of copyright protection, the book’s copyright expired at the end of 2021, causing Winnie-the-Pooh and the characters contained within it to enter the public domain in January 2022.
While these copyright extensions are important, the more interesting aspect of Winnie-the-Pooh’s journey into the public domain pertains to copyright transferability. In 1930, Milne first took advantage of his ability to transfer his copyright protections by signing an agreement with Stephen Slesinger, a “television-film producer, creator of comic-book characters, and pioneer in the licensing of characters for children.” Milne granted Slesinger “exclusive merchandising and other rights on the Pooh works in the United States and Canada.” This license lasted for the entirety of Winnie-the-Pooh’s copyright, which at the time extended through 1982. Slesinger subsequently granted these rights to Walt Disney Productions in 1961, and Milne’s estate also entered into a separate agreement with Disney around the same time. Milne’s agreement with Disney gave Disney nearly all of Pooh’s remaining copyright protections. This left Disney with nearly unrestricted access to use and develop the Winnie-the-Pooh characters into the popular cartoon versions.
The 1976 Copyright Act gave Milne’s estate an opportunity to reevaluate its agreements with Slesinger and Disney, as the Act allowed an author (or his heirs) to terminate a licensing agreement made under the 1909 Act. However, instead of terminating the licensing agreements, Milne’s estate opted to renegotiate its agreement with Disney in 1983 to receive a larger portion of royalties. Other than the royalty payment provisions, the new agreement had nearly identical terms to the old agreement, so Disney retained its nearly exclusive and unrestricted access to Winnie-the-Pooh. The licensing agreement was set to expire when the work entered the public domain, which at the time was less than 20 years away.
However, Milne’s estate in 1983 was unaware that the 1998 Copyright Extension Act would later grant Winnie-the-Pooh an additional 20 years of protection, further extending the duration of the licensing agreement as well as Disney’s exclusive rights to the work. Milne’s estate attempted to terminate the licensing agreement after the 1998 Act took effect, but the language of the 1998 Act only allowed for the termination of licensing agreements made before 1978. Because Disney and Milne executed a new contract in 1983 after renegotiating its terms, Milne’s estate was unable to terminate the agreement and Disney retained nearly exclusive rights to Winnie-the-Pooh until the book entered the public domain in 2022.
What Does This Mean for Pooh?
Now that Milne’s 1926 book has entered the public domain, “the plot, dialogue, and settings in that book are open for future creators,” along with the “appearance and traits” of any characters appearing in that book. This includes Piglet, Eeyore, Rabbit, Kanga, Roo, Owl, and Christopher Robin. Tigger, on the other hand, did not appear until 1928 in The House at Pooh Corner, so he does not enter the public domain until 2024.
While entering the public domain allows “anyone [to] adapt the 1926 book into a play, musical, film, or write a prequel or sequel,” the public does not have free reign to use many of Pooh’s modern characteristics. Any adaptations that Disney made to the character under the licensing agreements, such as giving him his signature red shirt, are still protected as derivative works. As such, Disney can still prevent the public from using its modified, well-known versions of Pooh.
The horror film, Blood and Honey, serves as an example of how creators can take advantage of Pooh’s entry into the public domain. This film, set to be released in 2023, “follows Pooh and Piglet as they go on a rampage after Christopher Robin abandons them for college.” While this film uses characters like Pooh and Piglet and refers to Milne’s original settings, the film refrains from using Disney’s red-shirted, cartoon-like version of Pooh.
Other artists have used their depictions of Pooh to explain and poke fun at copyright’s boundaries. For example, artist Lukey McGarry recently created a comic strip where Pooh refers to Disney’s copyright and jokingly explains to Christopher Robin that, “as long as I don’t put a little red shirt on, I can do as I like.”
How Will Disney Respond?
Though both the horror film and comic strip appear to be staying within the permissible boundaries of public domain, only time will tell if these works and others like them can escape intellectual property challenges brought by Disney. On one hand, Disney might actually benefit from the widespread renewed interest in Milne’s characters and, as a result, may refrain from challenging public use of Pooh. However, given Disney’s longstanding monopoly on Milne’s works, Disney may have trouble relinquishing its control over the characters. As a result, I presume that Disney’s last attempt to retain control over Pooh and his friends is yet to come.
Elisabeth Bruckner is a second-year law student at Northwestern Pritzker School of Law.
Introduction
The Supreme Court’s ruling in Dobbs v. Jackson Women’s Health Organization granted state legislatures the authority to regulate abortion. The Court’s decision quickly led states, such as Texas and Arkansas, to enact trigger bans for the procedure. Prior to the Court’s ruling, data brokers had already begun selling location data for individuals visiting abortion facilities through ordinary apps. This data often provided details to where the individual traveled from and how long they stayed at the facility.
In the wake of Dobbs, concerns have come to light regarding the potential misuse of sensitive personal health data originating from period tracking apps. Questions have arisen concerning whether “femtech” app data can be used to identify and prosecute individuals violating abortion laws. Due to lax federal laws and regulations in the United States, the onus falls on femtech companies to immediately and proactively find ways to protect users’ sensitive health data.
What is “Femtech’?
The term “femtech” was coined in 2016 by Ida Tin, the CEO and co-founder of period tracking app Clue. Femtech refers to health technology directed at supporting reproductive and menstrual healthcare. The femtech industry is currently estimated to have a market size between $500 million and $1 billion. Femtech apps are widely used with popular period-tracking app Flo Health touting more than 200 million downloads and 48 million monthly users.
Apps like Clue, Flo Health, and Stardust allow individuals to record and track their menstrual cycle to receive personalized predictions on their next period or their ovulation cycle. Although femtech apps collect highly sensitive health data, they are largely unregulated in the United States and there is a growing push for a comprehensive framework to protect sensitive health data that the apps collect from being sold or provided to third parties and law enforcement.
Current Regulatory Framework
Three federal agencies have regulatory authority over femtech apps – the Federal Trade Commission (“FTC”), United States Food and Drug Administration (“FDA”), and the Department of Health and Human Services (“HHS”). Their authority over femtech data privacy is limited in scope. Furthermore, while the FDA can clear the apps for contraceptive use, greater focus has been put on the FTC and HHS in regulating femtech. The Health Insurance Portability and Accountability Act (HIPAA), administered by the HHS, fails to protect sensitive health data from being collected and sold, and femtech apps are not covered under the Act. The FTC is currently exploring rules on harmful commercial surveillance and lax data security practices following President Joe Biden’s July 2022 executive order that encourages the FTC to “consider actions . . . to protect consumers’ privacy when seeking information about and provision of reproductive health care services.” The executive order’s definition of “reproductive healthcare services” does not, however, seem to include femtech apps. Thus, a massive gap remains in protecting sensitive health data consumers willingly provide to femtech app who may sell or provide such data to law enforcement or third parties. Femtech apps generally have free and paid versions for users, which makes the issue all the more immediate.
The unease based on potential misuse of health data collected by “femtech” apps heightened following the FTC’s complaint against Flo. The agency alleged the app violated Section 5 of the Federal Trade Commission Act (“FTCA”) by misleading consumers on how it handled sensitive health data. While the app promised to keep sensitive health data private, the FTC found the app was instead sharing this data with marketing and analytics firms, including Facebook and Google. Flo ultimately settled with the FTC, but the app refused to admit any wrongdoing.
FTC Commissioners Rohit Chopra and Rebecca Kelly Slaughter issued a joint statement following the settlement stating that, in addition to misleading consumers, they believed the app also violated the FTC’s Health Breach Notification Rule (“Rule”), which requires “vendors of unsecured health information . . . to notify users and the FTC if there has been an unauthorized disclosure.” The FTC refused to apply the Rule against Flo as such enforcement would have been “novel.” Such disclosures will help users navigate the post-Dobbs digital landscape, especially in light of news reports that law enforcement in certain states has begun to issue search warrants and subpoenas in abortion cases.
There is additional concern regarding femtech app’s potential location tracking falling into the hands of data brokers. The FTC recently charged Kochava, a data brokerage firm, with unfair trade practice under Section 5 of the FTCA for selling consumers’ precise geolocation data at abortion clinics. While Kochava’s data is not linked to femtech, in light of the FTC’s settlement with Flo, concerns of sensitive reproductive health data from femtech apps being sold is not out of the realm of possibility. Despite the FTC announcement on exploring new rules for commercial surveillance and lax data security, experts have expressed concern on whether such rulemaking is best done through the FTC or Congress. This is because the FTC’s rules are “typically more changeable than a law passed by Congress.”
As noted, most femtech apps are not covered under HIPAA nor are they required to comply. HIPAA encompasses three main rules under Title II: the Security Rule, the Privacy Rule, and the Breach Notification Rule. HIPAA is not a privacy bill, but it has grown to “provide expansive privacy protections for [protected health information] (“PHI”).” Due to the narrow definition of covered entity, there is little protection that can be provided to femtech app users under the current structure of HIPAA even though these apps collect health data that is “individually identifiable.”
Momentum for HIPAA to be amended so femtech may fall within the scope of covered entities may still fall short since HIPAA’s Privacy Rule permits covered entities to disclose protected health information (“PHI”) for law enforcement purposes through a subpoena or court-ordered warrant. While it does not require covered entities to disclose PHI, this permission could be troublesome in states hostile to abortion. Even if HIPAA’s definition of covered entities is expanded, it would still be up to the company to decide whether to disclose PHI to law enforcement. Some femtech companies, though, may be more willing to protect user data and have already begun to do so.
Future Outlook and What Apps Are Doing Post-Dobbs
In September 2022, Flo announced in an email to users that it was moving its data controller from the United States to the United Kingdom. The company wrote that this change meant their “data is handled subject to the UK Data Protection Act and the [General Data Protection Regulation].” Their privacy policy makes it clear that, despite this change, personal data collected is transferred and processed in the United States where it is governed by United States law. While Flo does not sell identifiable user health data to third parties, the company’s privacy policy states it may still share user’s personal data “in response to subpoenas, court orders or legal processes . . . .” While the GDPR is one of the strongest international data privacy laws, it still does not provide United States users with much protection.
In the same update, Flo introduced “anonymous mode” letting users access the app without providing their name, email, or any technical identifiers. Flo said this decision was made “in an effort to further protect sensitive reproductive health information in a post-Roe America.” The FTC, however, states that claims of anonymized data are often deceptive and that the data is easily traceable. Users may still be at risk of potentially having their sensitive health data handed over to law enforcement. Further, research shows femtech apps often have significant shortcomings with respect to making privacy policies easy to read and that users are often unaware of what their consent means.
While femtech has the potential to provide much-needed attention to a group often under-researched and underrepresented in medicine, the need to enhance current data privacy standards should be at the forefront for developers, legislators, and regulators. Although femtech companies may be incentivized to sell sensitive health data, their resources may be better spent lobbying for the passage of legislation like the American Data Privacy and Protection Act (“ADPPA”) and My Body, My Data Act otherwise the lack of data privacy measures may turn users away from femtech altogether. While no current reports show that menstruating individuals are turning away from femtech apps, it may be too soon to tell the effects post-Dobbs.
The ADPPA is a bipartisan bill that would be the “first comprehensive information privacy legislation” and would charge the FTC with the authority to administer the Act. The ADPPA would regulate “sensitive covered data” including “any information that describes or reveals the past, present, or future physical health, mental health, disability, diagnosis, or healthcare condition or treatment of an individual” as well as “precise geolocation information.” ADPAA’s scope would extend beyond covered providers as defined by HIPAA and would encompass femtech apps. The ADPPA would reduce the amount of data available through commercial sources that is available to law enforcement and give consumers more rights to control their data. The Act, however, is not perfect, and some legislators have argued that it would make it more difficult for individuals to bring forth claims against privacy violations. While it is unlikely that Congress will pass or consider ADPAA before it convenes in January 2023, it marks a start to long-awaited federal privacy law discussions.
On a state level, California moved quickly to enact two bills that would strengthen privacy protections for individuals seeking abortion, including prohibiting cooperation with out-of-state law enforcement regardless of whether the individual is a California resident. Although California is working to become an abortion safe haven, abortion access is costly and individuals most impacted by the Supreme Court’s decision will likely not be able to fund trips to the state to take advantage of the strong privacy laws.
As menstruating individuals continue to navigate the post-Dobbs landscape, transparency from femtech companies should be provided to consumers with regard to how their reproductive health data is being collected and how it may be shared, especially when it comes to a growing healthcare service that individuals are exploring online - abortion pills.
Angela Petkovic is a second-year law student at Northwestern Pritzker School of Law.
In August 2022, over two and a half years after the start of the Covid-19 pandemic, Moderna sued Pfizer and BioNTech for patent infringement. Specifically, Moderna claimed that Pfizer and BioNTech used its patented mRNA technology to develop their Covid-19 vaccine. Covid’s swift, widespread, and devastating effects and the urgent need for a vaccine accelerated a typically years-long research and development process into one short year. Although public health and humanitarian aid were undoubtedly at the forefront of vaccine developers’ minds, intellectual property (IP) rights and their economic incentives were a significant factor as well.
In the United States, IP laws regarding patent protection are largely based on utilitarian and economic theories. The monopolistic rights given to patentholders and the typical damages for patent infringement reflect these theoretical foundations. In its complaint, Moderna seeks “fair compensation” for Pfizer’s use of the mRNA technology, essentially a cut of Pfizer’s profits, which could potentially amount to billions of dollars from a period of only two to three years. Despite the billion-dollar vaccine industry, the strong economic bases of patent protection are potentially at odds with promoting scientific innovation. The critical need for worldwide Covid vaccines to save potentially millions of lives underscored whether utilitarianism and economics are always the best rationales for IP. Public policy considerations, including public health and humanitarian aid, may justify at least partial waiver of IP rights in certain circumstances. Even Moderna acknowledged this, professing in its complaint its “belief that intellectual property should never be a barrier” to the vaccine. The company initially pledged not to assert its Covid-19 patent rights against fellow Covid vaccine developers to reduce barriers to global vaccine access. However, billions of dollars in competitors’ profits and an amended pledge later, the biotech industry is now watching an imminent IP battle between pharmaceutical giants. This current situation is unique in many respects, due to not only the scientific, economic, and social significance of the patents at stake, but also the companies’ global reputations as leading medical innovators.
Moderna’s complaint alleges that Pfizer and BioNTech infringed Moderna’s patents on mRNA technology used between 2011 and 2016 in other vaccines. In the company’s press release, Moderna’s CEO also emphasized its prominence in the field of RNA technology and the substantial time and resources used to develop the technology that Pfizer copied. The infringement focuses on the chemical modifications Moderna introduced to mRNA to improve immune system evasion and the lipid nanoparticle formulation used to deliver the modified mRNA.
Like most patent infringement plaintiffs, Moderna has financial stakes as a top priority. Moderna ultimately seeks a portion of Pfizer’s profits from its Covid vaccine, citing Pfizer’s unjust “substantial financial windfall” from its allegedly unauthorized use of Moderna’s technology. Pfizer’s 2021 revenue from its Covid vaccine totaled over $36 billion, and it expects another $32 billion in 2022. Moderna also seeks enhanced treble damages, suggesting willful or bad faith infringement from Pfizer. These are bold claims coming from Moderna, a relatively young company founded in 2010, against the nearly two-century-old industry giant, Pfizer.
This lawsuit demonstrates the utilitarian and economic theories of IP law, particularly patent law, in the United States. Under these theories, patent protection incentivizes invention and innovation by giving the inventor a temporary but strong monopoly on their invention. This monopoly allows the inventor to exclude others from using their information and knowledge without authorization. Information is non-rivalrous and non-excludible and would otherwise fall victim to public goods problems. For example, free riders can wait for someone else to create the invention, and then replicate the invention at a much lower cost. The original inventor would thus be disincentivized to disclose their invention for fear of losing valuable profits in a market saturated with copycats. Patent rights prevent these detriments of information as a public good by giving the inventor legal control over dissemination of the information. Applying this theory here, Moderna would argue that its previous patents represented a tradeoff that the company would publicly disclose its valuable information on mRNA technology. In return, Moderna would receive a legally protected right to exclude others, including Pfizer, from using the information.
These economic theories are based on patent rights’ essential function to tightly control information use; however, free dissemination of information is critical for scientific research, including vaccine development. The utilitarian foundations of U.S. IP law may not align with vaccine research goals, particularly in urgent pandemic circumstances. In these time-sensitive situations, allowing simultaneous inventors access to each other’s research developments may best serve the public interest. Some critics even argue that patents and economic incentives are entirely unneeded for vaccine research and development. The highly specialized technical know-how required and the complex regulatory framework for entering the vaccine market naturally weed out copycat competitors and create a monopoly position without patent rights. Further, vaccine manufacturers are in a favorable position selling a product whose demand reliably far outstrips supply.
Despite this view, patent rights will likely still play a role in pandemic vaccine development. However, this role may be more detrimental than beneficial to inventors and ultimately consumers. Although an inventor would prefer to keep a tightly guarded monopoly on their lucrative vaccine technology, this economically driven IP strategy may exacerbate the pandemic. Research responses to pandemics may require inventors to relinquish potential profits from strong information monopolies in exchange for rapid information sharing to encourage life-saving follow-on innovation. Enforcing pandemic research patent rights can significantly limit advancements in vaccine development, the opposite of the intended goal to serve public health.
Moderna recognized this dilemma and in October of 2020, it initially pledged to not enforce its IP rights related to Covid-19 vaccines during the pandemic. Considering the myriad economic benefits of IP rights, this pledge may have seemed financially counterproductive for Moderna. However, it demonstrated that Moderna also knew of the unprecedented public health and policy concerns at stake and did not want to deter other researchers from simultaneously developing Covid vaccines. However, in March 2022, Moderna updated its IP pledge, instead committing to never enforcing its Covid-19 patents against 92 middle- and low-income countries, thus making this lawsuit possible. It remains a question whether the original October 2020 pledge caused any parties to reasonably rely on Moderna’s assurance and whether there may be legal contract obligations to Pfizer or other vaccine developers. Regardless of potential contract law disputes, the urgent pandemic needs for Covid vaccines drove Moderna to its “Global Commitment to Intellectual Property Never Being a Barrier to COVID-19 Vaccine Access” cited in its complaint. Money and economic benefits are a significant motivating factor in the lawsuit, but the public health and humanitarian considerations underly the policy concerns of the claim.
The Covid pandemic forced the IP field, the scientific community, and the global public health sector to reconsider the role of economic and utilitarian theories in patent rights. Although innovators deserve financial rewards for being the first to develop and license their vaccines, the intended widespread benefit of this biotechnology can be significantly limited with overly restrictive information monopolies. Due to the scope and effects of Covid, vaccines have taken a new meaning, representing the potential return to the pre-pandemic “normal” and restoring society and the economy. Thus, the patent rights for Covid vaccines might have more than just economic value; they also bring reputational influence of goodwill and societal stabilization. Other areas of IP, such as copyright and trademark law, are less rooted in utilitarianism and are partly based on the personhood theory, which relates the IP to the creator’s sense of self and identity. Patent law is less concerned with traditional expressive elements of creation. However, the humanitarian nature of Covid vaccine development and distribution may implicate some personhood concerns of distributive justice and fairness. During such global health crises, reducing some of IP’s economic barriers to information and focusing on the personal effects on vaccine distribution may better serve the public interest.
Overall, IP scholars and policymakers should consider how non-economic theories may be, at times, better suited for IP protection and can help shape a more dynamic patent law system. While patent law should still strive to incentivize innovation and creation, policies must also acknowledge the effects of purely economic motivations on patient health and global health disparities. The Moderna v. Pfizer lawsuit illustrates the mismatches between economic foundations of patent law, biotechnological and pharmaceutical innovation, and emergency or pandemic situations.
Shelby Yuan is a second-year JD-PhD student at the Northwestern Pritzker School of Law.
Within the past decade, companies outside of the traditional financial services firms have disrupted the financial industry due to technology shifts. Gaming companies now offer in-game currencies creating virtual economies and technology companies like Venmo and Zelle have disrupted the digital wallet space. With the creation of new virtual economies comes additional risk for consumers. These market entrants create new venues for cybercriminal activity, such as scams and money laundering.
Video Games and Microtransactions
In-game currency in video games pre-dates the current trend of digital currency. Many video games give users the ability to expand their experience by creating a virtual economy. Players engage in microtransactions where real currency is exchanged for virtual currency to use within a video game. The video game industry generated $21.1 billion in revenue in 2020 and has risen in recent years due to the pandemic which led to a rise in people seeking entertainment through online gaming.
Many game companies incorporate in-game currency to extend a player’s game time. For example, Minecraft, a sandbox video game with over 238 million copies sold, developed its own currency called “coins” as well as a marketplace within the game. Other games with active in-game economies include Second Life and World of Warcraft. While the intention of marketplaces in video games is to give gamers new and exciting features that drive them to increase their play time, cyber criminals have tapped these platforms to engage in money laundering and fraud. These games have players from all over the world, generating risks of cross-border money laundering and financing terrorism.
There are several ways a cybercriminal can engage in money laundering. The first is through using Skins. “Skins” are customized looks or accessories that gamers buy in-app to enhance their characters and extend their play time. These items are purchased, traded, or earned within the game. Another way is through third-party skin gambling sites such as CSGOEmpire, or Thunderpick where people can bid on these add-ons in exchange for cash. People use multiple accounts to build their reputation, and then sell items to other members in exchange for cash, with the option to withdraw those funds. Another way that money laundering can occur is when criminals use game platforms to clean dirty money. They load their account with the dirty money using stolen credit cards or other means, then transact with others several times until the money is clean and withdraw those new funds. Lastly, cybercriminals leverage stolen credit cards to engage in money laundering. They build profiles in digital gaming economies with lots of in-game features, such as skins or in-game currency. Cybercriminals will then sell these accounts on the secondary market to another user in exchange for cash.
Money Laundering in E-Payments
With Covid-19, we also saw an increase in fraud through use of money transfer apps. Criminals find individuals to deposit funds into an electronic payment app and then move funds to various accounts in order to clean the money. The Secret Service has over 700 pending investigations regarding payment fraud specifically related to COVID-19 relief funds. While these apps are easy to use and provide flexibility to customers and businesses, oftentimes at no cost, they also have led to an increase in fraud as well as a lack of consumer protection. While the transactions may be small at the individual level, used often to pay someone back for a meal or another shared expense, in aggregate these digital payment apps see huge traffic. Customers transferred $490 billion through Zelle and $230 billion was through Venmo in 2021. The rise in popularity of digital payment channels have led to more avenues for fraudulent activity.
There are various types of scams that cybercriminals can engage in using digital payment services. Users can be targeted for phishing scams via text message. They also can be targeted for a reverse charge: a stolen credit card is used for the transaction, the goods are delivered, and then a few days later the charge reverses because the card is illegitimate, but the goods are already out of the seller’s hands. Additionally, the goods themselves may not exist: a buyer might transact on Zelle or Venmo with the intention of purchasing the product, authorize a payment, but never receive the item.
With the rise in digital payment services as well as fraud, there is a question about whether consumers should bear responsibility for their actions or if they deserve protection from the platform. Zelle was created in 2017 by banks to promote digital transactions. However, these same banks claim that they are not liable to protect consumers against fraud because they authorize each transaction. Additionally digital payment platforms are starting to participate in cryptocurrency, another area in which legislators are looking to regulate to reduce fraud and protect the economy.
Relevant Regulations and Challenges
There are various regulations that impact the use of digital currency services as well as video games in relation to money laundering and fraud; however, they may not be comprehensive enough to apply to these new platforms.
Title 18 §1960 of the U.S. Code criminalizes unlicensed operation of money transmitting businesses. This regulation was developed by Congress in response to money launderers’ shift towards nonbank financial institutions in the 1990s. While digital payment services would qualify as engaging in “money transmitting,” it is unclear if video games, and their in-game currencies would fall under the code’s definitions of “funds.” In-game currencies could be considered funds due to the existence of vast secondary markets. Accounts are often sold between users, and skins are auctioned on dedicated platforms. On the other hand, courts have found that in-game currency and virtual items do not hold real-world value and fail to meet the meaning of “money” (see Soto v. Sky Union, LLC, a class action lawsuit where the court held that in-game currency did not hold real-world value because they could not be cashed out into real currency).
Additionally, the European Global Data Protection Regulation (”GDPR”) challenges safeguards against money laundering through video games and digital payment services through individuals‘ “right to be forgotten,” which can impede traceability of money laundering and fraud identification.
The US Consumer Financial Protection Bureau (“CFPB”) also has established regulations for unauthorized transfers. Under 12 CFR §1005.2, the Code of Federal Regulations defines unauthorized transfers as ones which are “initiated by a person other than the consumer without actual authority to initiate the transfer and from which the consumer receives no benefit,” but does not include a transaction by someone who was given access to the device to make the transaction. Additionally, the liability is capped at $50 or $500 depending on if they provide notice to the financial institution.
The federal government, under the USA PATRIOT Act, also regulates money transfer services. The intention of the Act is to lay groundwork to deter and punish terrorist attacks through law enforcement and money laundering protection. Venmo, which qualifies as a money transfer services, had to implement a Customer Identification Program and collect additional information (e.g. Social Security Number) to verify the identities of users making transactions in accordance with the Act. While the Act intends to crackdown to reduce money laundering criminals are now instead looking for other venues to transact. Video games serve as an alternative as they are full of users engaging in micro transactions, thereby making it easier for money launderers to blend in and harder for government agents to catch.
Lastly, there are efforts underway to develop and review Anti-Money Laundering (“AML”) regulations. The European Commission published draft regulations in July 2021 to establish an EU AML authority and impose a single rulebook to coordinate approaches. While these regulations intend to restrict cybercriminals, it is unclear if these regulations are robust enough to protect consumers against cybercriminal activity in this digital age. Congress and regulators need to keep a close watch to new market entrants in digital payments to ensure regulations are comprehensive and continue to protect consumers against potential fraud in all venues.
Kathleen Denise Arteficio is a third-year JD-MBA student at the Northwestern Pritzker School of Law.
INTRODUCTION
“Zombies” may be pure fiction in Hollywood movies, but they are a very real concern in an area where most individuals would least expect – trademark law. A long-established doctrine in U.S. trademark law deems a mark to be considered abandoned when its use has been discontinued and where the trademark owner has no intent to resume use. Given how straightforward this doctrine seems, it is curious why the doctrine of residual goodwill has been given such great importance in trademark law.
Residual goodwill is defined as customer recognition that persists even after the last sale of a product or service have concluded and the owner has no intent to resume use. Courts have not come to a clear consensus on how much weight to assign to residual goodwill when conducting a trademark abandonment analysis. Not only is the doctrine of residual goodwill not rooted in federal trademark statutes, but it also has the potential to stifle creativity among entrepreneurs as the secondhand marketplace model continues to grow rapidly in the retail industry.
This dynamic has led to a phenomenon where (1) courts have placed too much weight on the doctrine of residual goodwill in assessing trademark abandonment, leading to (2) over-reliance on residual goodwill, which can be especially problematic given the growth of the secondhand retail market, and finally, (3) over-reliance on residual goodwill in the secondhand retail market will disproportionately benefit large corporations over smaller entrepreneurs.
A. The Over-Extension of Residual Goodwill in Trademark Law
A long-held principle in intellectual property law is that “[t]rademarks contribute to an efficient market by helping consumers find products they like from sources they trust.” However, the law has many forfeiture mechanisms that can put an end to a product’s trademark protection when justice calls for it. One of these mechanisms is the abandonment doctrine. Under this doctrine, a trademark owner can lose protection if the owner ceases use of the mark and cannot show a clear intent to resume use. Accordingly, the abandonment doctrine encourages brands to keep marks and products in use so that they cannot merely warehouse marks to siphon off market competition.
The theory behind residual goodwill is that trademark owners may deserve continued protection even after a prima facie finding of abandonment because consumers may associate a discontinued trademark with the producer of a discontinued product. This doctrine is primarily a product of case law rather than deriving from trademark statutes. Most courts will not rely on principles of residual goodwill alone in evaluating whether a mark owner has abandoned its mark. Instead, courts will often consider residual goodwill along with evidence of how long the mark had been discontinued and whether the mark owner intended to reintroduce the mark in the future.
Some courts, like the Fifth Circuit, have gone as far as completely rejecting the doctrine of residual goodwill in trademark abandonment analysis and will focus solely on the intent of the mark owner in reintroducing the mark. These courts reject the notion that a trademark owner’s “intent not to abandon” is the same as an “intent to resume use” when the owner is accused of trademark warehousing. Indeed, in Exxon Corp. v. Humble Exploration Co., the Fifth Circuit held that “[s]topping at an ‘intent not to abandon’ tolerates an owner’s protecting a mark with neither commercial use nor plans to resume commercial use” and that “such a license is not permitted by the Lanham Act.”
The topic of residual goodwill has gained increased importance over the last several years as the secondhand retail market has grown. The presence of online resale and restoration businesses in the fashion sector has made it much easier for consumers to buy products that have been in commerce for several decades and might contain trademarks still possessing strong residual goodwill. Accordingly, it will be even more crucial for courts and policymakers to take a hard look at whether too much importance is currently placed on residual goodwill in trademark abandonment analysis.
B. Residual Goodwill’s Increasing Importance Given the Growth of the Secondhand Resale Fashion Market
Trademark residual goodwill will become even more important for retail entrepreneurs to consider, given the rapid growth in the secondhand retail market. Brands are using these secondhand marketplaces to extend the lifecycles of some of their top products, which will subsequently extend the lifecycle of their intellectual property through increased residual goodwill.
Sales in the secondhand retail market reached $36 billion in 2021 and are projected to nearly double in the next five years to $77 billion. Major brands and retailers are now making more concerted efforts to move into the resale space to avoid having their market share stolen by resellers. As more large retailers and brands extend the lifecycle of their products through resale marketplaces, these companies will also likely extend the lifespan of their intellectual property based on the principles of residual goodwill. In other words, it is now more likely for residual goodwill to accrue with products that are discontinued by major brands and retailers now since those discontinued products are made available through secondhand marketplaces.
The impact of the secondhand retail market on residual goodwill analysis may seem like it is still in its early stages of development. However, the recent Testarossa case, Ferrari SpA v. DU , out of the Court of Justice of the European Union is a preview of what may unfold in the U.S. In Testarossa, a German toy manufacturer challenged the validity of Ferrari’s trademark for its Testarossa car model on the grounds that Ferrari had not used the mark since it stopped producing Testarossas in 1996. While Ferrari had ceased producing new Testarossa models in 1996, it had still sold $20,000 in Testarossa parts between 2011 and 2017. As a result, the CJEU ultimately ruled in Ferrari’s favor and held that production of these parts constituted “use of that mark in accordance with its essential function” of identifying the Testarossa parts and where they came from.
Although Ferrari did use the Testarossa mark in commerce by selling car parts associated with the mark, the court’s dicta in the opinion referred to the topic of residual goodwill and its potentially broader applications. In its reasoning, the CJEU explained that if the trademark holder “actually uses the mark, in accordance with its essential function . . . when reselling second-hand goods, such use is capable of constituting ‘genuine use.’”
The Testarossa case dealt primarily with sales of cars and automobile parts, but the implications of its ruling extend to secondhand retail, in general. If the resale of goods is enough to qualify as “genuine use” under trademark law, then this provides trademark holders with a much lower threshold to prove that they have not abandoned marks. This lower threshold for “genuine use” in secondhand retail marketplaces, taken together with how courts have given potentially too much weight to residual goodwill in trademark abandonment analyses, could lead to adverse consequences for entrepreneurs in the retail sector.
C. The Largest Brands and Retailers Will Disproportionately Benefit from Relaxed Trademark Requirements
The increasingly low thresholds for satisfying trademark “genuine use” and for avoiding trademark abandonment will disproportionately benefit the largest fashion brands and retailers at the expense of smaller entrepreneurs in secondhand retail. Retail behemoths, such as Nike and Gucci, will disproportionately benefit from residual goodwill and increasingly relaxed requirements for trademark protection since these companies control more of their industry value systems. This concept will be explained in more detail in the next section.
Every retail company is a collection of activities that are performed to design, produce, market, deliver, and support the sale of its product. All these activities can be represented using a value chain. Meanwhile, a value system includes both a firm’s value chain and the value chains of all its suppliers, channels, and buyers. Any company’s competitive advantages can be best understood by looking at both its value chain and how it fits into its overall value system.
In fashion, top brands and retailers, such as Nike and Zara, sustain strong competitive advantages in the marketplace in part because of their control over multiple aspects of their value systems. For example, by offering private labels, retailers exert control over the supplier portion of their value systems. Furthermore, by owning stores and offering direct-to-consumer shipping, brands exert control over the channel portion of their value systems. These competitive advantages are only heightened when a company maintains tight protection over their intellectual property.
As portrayed in the figure below , companies maintain the strongest competitive advantages in cell one when they are advantageously positioned relative to owners of complementary assets, and they maintain strong intellectual property protection. In such situations, an innovator will win since it can derive value at multiple sections of its value system using its intellectual property.
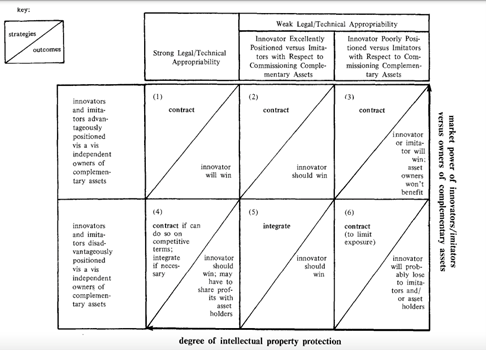
CONCLUSION
Although there is little case law on the relevance of residual goodwill and secondhand retail marketplaces, it is only a matter of time until the largest fashion brands and retailers capitalize on increasingly low thresholds for demonstrating trademark “genuine use.” Courts and policymakers should now stay alert of these potential issues when dealing with trademark abandonment matters.
Rohun Reddy is a third-year JD-MBA student at the Northwestern Pritzker School of Law.
In August 2020, Marlene Stollings, the head coach of Texas Tech Women’s Basketball Team, allegedly forced her players to wear heart rate monitors during practice and games. Stollings would subsequently view the player data and reprimand each player who did not achieve their target heart rates. It could be argued that Stollings was simply pushing her players to perform better, however former player Erin DeGrate described Stollings’ use of the data as a “torture mechanism.” This is just one reported example of how athletic programs use athlete data collected from wearable technology to the student athlete’s detriment.
As of 2021 the market for wearable devices in athletics has a $79.94 billion valuation and is expected to grow to $212.67 billion by 2029. The major market competitors in the industry consist of Nike, Adidas, Under Armour, Apple, and Alphabet, Inc. so the expected growth comes as no surprise. Some wearable technology is worn by everyday consumers to simply track how many calories they have burned in a day or whether they met their desired exercise goals. On the other hand, professional and college athletes use wearable technology to track health and activity data to better understand their bodies and gain a competitive edge. While professional athletes can negotiate which types of technology they wear and how the technology is used through their league’s respective collective bargaining agreement, collegiate athletes do not benefit from these negotiation powers. Universities ultimately possess a sort of “constructive authority” to determine what kind of technology students wear, what data is collected, and how that data is used without considering the student athlete’s level of comfort. This is because if the student-athlete chooses to-opt out of wearable technology usage it may hinder their playing time or lead to being kicked off the team.
Studies show that collecting athlete biometric data has a positive effect on a player’s success and helps reduce possible injury. For instance, professional leagues utilize wearables for creating heat maps to analyze an athlete’s decision-making abilities. The Florida State Seminole basketball program also routinely uses wearables to track and monitor early signs of soft tissue damage which helped reduce the team’s overall injury rate by 88%. However, there are significant trade-offs including the invasion of an athlete’s privacy and possible misuse of the data.
Section I of this article will examine the different types of information collected from athletes and how that information is being collected. Section II will discuss a college athlete’s right to privacy under state biometric laws. Section III will discuss how data privacy laws are changing with respect to collecting athlete biometric data. Last, section IV will discuss possible solutions to collecting biometric data.
II. What Data is Collected & How?
Many people around the country use Smart Watch technology such as Fitbits, Apple Watches, or Samsung Galaxy Watches to track their everyday lifestyle. Intending to maintain a healthy lifestyle, people usually allow these devices to monitor the number of steps taken throughout the day, how many calories were burned, the variance of their heart rate, or even their sleep schedule. On the surface, there is nothing inherently problematic about this data collection, however, biometric data collected on college athletes is much more intrusive. Athletic programs are beginning to enter into contractual relationships with big tech companies to provide wearable technology for their athletes. For example, Rutgers University football program partnered with Oura to provide wearable rings for their athletes. Moreover, the types of data these devices collect include blood oxygenation levels, glucose, gait, blood pressure, body temperature, body fatigue, muscle strain, and even brain activity. While many college athletes voluntarily rely on wearable technology to develop a competitive edge, some collegiate programs now mandate students wear the technology for the athletic program to collect the data. Collegiate athletes do not have the benefit of negotiations or the privileges of a collective bargaining agreement, but the athletes do sign a national letter of intent which requires a waiver of certain rights in order to play for the University. Although college athletes have little to no bargaining power, they should be given the chance to negotiate this national letter of intent to incorporate biometric data privacy issues because it is ultimately their bodies producing the data.
II. Biometric Privacy Laws
Currently, there are no federal privacy laws on point that protect collecting student athlete biometric data. Nonetheless, some states have enacted biometric privacy statutes to deal with the issue. Illinois, for example, which houses thirteen NCAA Division I athletic programs, authorized the Biometric Information Privacy Act (BIPA) in 2008. BIPA creates standards for how companies in Illinois must handle biometric data. Specifically, BIPA prohibits private companies from collecting biometric data unless the company (1) informs the individual in writing that their biometric data is being collected or stored, (2) informs the individual in writing why the data is being collected along with the duration collection will continue for and (3) the company receives a written release from the individual. This is a step in the right direction in protecting athletes’ privacy since the statute’s language implies athletes would have to provide informed consent before their biometric data is collected. However, BIPA does not apply to universities and their student-athletes since they fall under the 25(c) exemption for institutions. Five other Illinois courts, including a recent decision in Powell v. DePaul University, explain the 25(c) exemption extended to “institutions of higher education that are significantly engaged in financial activities such as making or administering student loans.”
So, although Illinois has been praised for being one of the first states to address the emerging use of biometric data by private companies, it does not protect collegiate athletes who are “voluntarily” opting into the wearable technology procedures set by their teams.
III. Data Collection Laws are Changing
While BIPA does not protect collegiate athletes, other states have enacted privacy laws that may protect student-athletes. In 2017 the state of Washington followed Illinois’ footsteps by enacting its own biometric privacy law that is substantively similar to the provisions in BIPA. But the Washington law contains an expanded definition of what constitutes “biometric data.” Specifically, the law defines biometric identifiers as “data generated by automatic measurements of an individual’s biological characteristics, such as a fingerprint, voiceprint, eye retinas, irises or other unique biological patterns or characteristics that are used to identify a specific individual.” By adding the two phrases, “data generated by automatic measurements of an individual’s biological characteristics,” and “other biological patterns or characteristics that is used to identify a specific individual,” the Washington law may encompass the complex health data collected from student-athletes. The language in the statute is broad and thus likely covers an athlete’s biometric data because it is unique to that certain individual and could be used as a characteristic to identify that individual.
IV. Possible Solutions to Protect Player Biometric Data
Overall, it’s hard to believe that biometric data on student-athletes will see increased restrictions any time soon. There is too much on the line for college athletic programs to stop collecting biometric data since programs want to do whatever it takes to gain a competitive edge. Nonetheless, it would be possible to restrict who has access to athletes’ biometric data. In 2016, Nike and the University of Michigan signed an agreement worth $170 million where Nike would provide Michigan athletes with apparel and in return, Michigan would allow Nike to obtain personal data from Michigan athletes through the use of wearable technology. The contract hardly protected the University’s student-athletes and was executed in secrecy seeing its details were only revealed after obtaining information through the Freedom of Information Act. Since the University was negotiating the use of the student athlete’s biometric data on the athlete’s behalf, it can likely be assumed that the University owns the data. Therefore, athletes should push for negotiable scholarship terms allowing them to restrict access to their biometric data and only allow the athletic program’s medical professionals to obtain the data.
One would think that HIPAA protects this information from the outset. Yet there is a “general consensus” that HIPAA does not apply to information collected by wearables since (a) “wearable technology companies are not considered ‘covered entities’, (b) athletes consent to these companies having access to their information, or (c) an employment exemption applies.” Allowing student-athletes to restrict access before their college career starts likely hinders the peer pressure received from coaches to consent to data collection. Further, this would show they do not consent to companies having access to their information and could trigger HIPAA. This would also cause the information to be privileged since it is in the hands of a medical professional, and the athlete could still analyze the data with the medical professional on his or her own to gain the competitive edge biometric data provides.
Anthony Vitucci is a third-year law student at Northwestern Pritzker School of Law.
Introduction
News headlines about facial recognition technology primarily focus on the government’s use and misuse of the technology. Likewise, technology companies and legislators frequently advocate against the government’s use of facial recognition tools to conduct mass surveillance or generate leads in investigations. For example, following widespread claims of the technology’s racial bias, Amazon, IBM, and Microsoft announced that they would stop selling facial recognition tools to law enforcement agencies. And following the arrest of an innocent black man who was falsely identified by facial recognition, major cities like San Francisco and Boston banned law enforcement from using the technology.
However, as industry commentators focus on the government’s use of facial recognition tools, private businesses in the U.S. regularly deploy facial recognition technology to secretly surveil their customers. Companies rely on the technology to gather information about customers’ identities and demographics to tailor their marketing strategies, monitor customers within stores, or sell the information to third parties. Since there are no federal regulations governing the technology, commercial uses of facial recognition technology remain relatively unchecked, even as companies invade their customers’ privacy rights without any warning.
How Does Facial Recognition Technology Work?
Based on photos or still images, facial recognition technology scans, maps, and analyzes the geometry of a person’s face to verify their identity or collect information about their behavior. When mapping a face, the technology creates a mathematical formula — called a facial signature — based on the person’s distinct facial features, such as the distance between their eyes. Facial recognition systems can create and store facial signatures for each scanned image containing a face. When a user uploads a new photo, the system cross-references the generated facial signature with existing ones in the database and can verify the person’s identity with a matched signature.
Businesses have created databases of facial signatures to identify customers of interest in future video footage. In addition, businesses can use facial recognition software from companies like Clearview AI, which cross-references an uploaded photo against billions of public images to verify a person’s identity. Clearview AI is known to offer free trials of its software, luring businesses and rogue employees into using the technology. With such easy access to facial recognition software, private use of the technology has proliferated, hardly slowed by regulatory barriers.
Commercial Uses of Facial Recognition Technology
No matter the industry, facial recognition can help businesses glean more information about their customers, make informed business decisions, and increase their revenues. Shopping malls and mega-stores like Macy’s, Rite-Aid, Apple, and Walmart have used facial recognition to identify shoplifters, target loyal customers, and track customers’ reactions within the store. Amazon has sold facial recognition technology that assesses customers’ faces to discover whether they are attentive or indifferent to certain displays. While customers are surely aware these mega-stores have security cameras, they are likely unaware these stores may know their name, home address, how many times they’ve frequented the location, and whether they are happy with their in-store experience. Outside of retail stores, in cities like Miami, thousands of Uber and Lyft drivers have digital tablets in their backseats that use facial recognition technology to assess a rider’s age, gender, and demographics, in order to display ads tailored to the rider’s perceived characteristics.
In states without biometric privacy laws, any citizen who shops at a mall or grocery store, or attends a concert or sports game, will likely be the subject of unsuspecting facial recognition. Additionally, facial recognition tools can even identify an individual who rarely shows their face in public. Clearview AI created a facial recognition database by scraping ten billion images from public websites. Clearview analyzed the images and developed facial signatures for nearly half the U.S. population.
As of 2020, more than 200 companies had accounts with Clearview, including professional sports leagues, casinos, fitness centers, and banks. These companies can upload a photo of an individual’s face — pulled from security footage or driver’s licenses — and cross-reference it against Clearview’s database to find a match. With limited regulation and easy access to facial recognition tools, consumers will face the technology’s adverse consequences, such as misidentifications and loss of privacy rights.
Misidentifications and Privacy Risks
The accuracy of facial recognition technology to correctly identify a person depends on their age, gender, or race. Research from the National Institute of Standards and Technology revealed that facial recognition systems are less accurate when identifying people of color. The algorithms are more likely to misidentify African Americans, Native Americans, and Asians compared to Caucasians. Researchers also have found these algorithms to be less accurate when identifying women, transgender individuals, and children.
Misidentification can carry damaging consequences to an individual’s liberty and dignity. Robert Williams, the black man who was wrongfully arrested based on a facial recognition match, was a victim of misidentification. These same misidentifications are likely occurring at private establishments, where security guards use the technology to scan for known criminals and remove purported “matches” from their stores.
In addition to misidentifications, facial recognition technology intrudes on an individual’s right to privacy. The technology allows companies to identify customers without their consent, collecting information about customers’ demographics and preferences. Furthermore, companies that store facial templates are subject to data breaches, where thousands of their customers’ faceprints could become compromised. Unlike online passwords, a stolen faceprint is indefinitely compromised — a customer cannot change their faceprint. Last year, thousands of scammers in the U.S. tried using stolen faceprints to fraudulently obtain government-assistance benefits. As facial recognition technology grows, bad actors will attempt to use stolen faceprints for financial gain.
Federal, State, and Local Regulations
There are no federal regulations curbing the private use of facial recognition technology, but Congress’s interest in regulating the technology is increasing. Legislators introduced three separate bills to regulate facial recognition technology in the past few years, yet none passed the introduction stage.
One of the bills introduced in the Senate, the Commercial Facial Recognition Privacy Act, would have required all private entities to obtain explicit consent from customers before collecting faceprint data. The bill’s consent requirement is based on the Illinois Biometric Information Privacy Act (BIPA), one of only three state-enacted biometric privacy laws.
BIPA requires businesses that use facial recognition technology to obtain consent from consumers before collecting their faceprint data. It also requires these businesses to provide information about how they protect and store the biometric data. BIPA permits individuals to sue companies who violate any requirement in the statute and offers significant statutory damages for violations. In February 2021, Facebook paid out $650 million to settle a BIPA class-action lawsuit. To date, more than 800 BIPA class action lawsuits have been filed against Illinois businesses.
Despite BIPA’s teeth, businesses can freely use facial recognition in almost every other state. Texas and Washington are the only other states with biometric privacy laws that regulate commercial use of the technology. Yet, neither state permits citizens to sue companies for violating the statute, meaning there is much less pressure to comply. Enforcement lies with each state’s attorney general, who can impose civil penalties on violators.
Fortunately, bans on private use are growing at the city level. In September 2020, Portland, Oregon, became the first municipality to ban private entities from using facial recognition in public places, such as shopping malls. Since then, two other cities have followed suit. New York City now requires commercial establishments to post notices when using facial recognition technology, and Baltimore banned all private sector use of the technology, even subjecting violators to criminal penalties. The recent wave of restrictions at the city level indicates that regulations may first arise where the commercial sector flourishes — in major cities.
Calls for Regulation and Future Outlook
Despite the pervasive commercial use of facial recognition technology, sixty percent of Americans are unaware that retail stores use the technology. This lack of awareness stems in part from the lack of regulation. Aside from a few states and a handful of cities, most businesses are unregulated: free to implement facial recognition tools without warning their customers. So far, calls for regulation have primarily come from companies that have developed facial recognition technology themselves: Microsoft, IBM, and Amazon. While these calls may be aimed at influencing friendly regulations, Microsoft’s President Brad Smith has called for legislation requiring stores to provide notice and obtain consent, similar to BIPA’s consent requirement. As BIPA has revealed, requiring businesses to obtain consent from consumers would at least hold businesses accountable for their facial recognition uses.
Nevertheless, some businesses may not wait for enacted legislation before shelving their facial recognition products. In November 2021, Meta announced that Facebook will no longer use facial recognition software and plans to delete the faceprint data of one billion Facebook users. Meta’s decision was motivated by concerns about the technology’s “place in our society.” This drastic move may prompt other industry leaders to start influencing the future treatment of facial recognition technology, with the hopes of clearing up the current regulatory uncertainty that threatens innovation and investment. While some may question Meta’s sincerity or true motives, its decision could foreshadow an era of much-needed regulatory action.
Michael Willian is a third-year law student at Northwestern Pritzker School of Law.
I. Introduction
The COVID-19 pandemic has brought the issues of personal privacy and biometric data to the forefront of the American legal landscape. In an increasingly digital world, privacy laws are more important than ever. This reality is especially true in the context of remote workplaces, where employers have facilitated a digital migration through a variety of means. The platforms employers use have the propensity to violate personal privacy through the capture and storage of sensitive biometric information. In response, states across the nation are exploring solutions to the potential privacy issues inherent in the collection of biometric data. One of the first states to do so was Illinois, enacting a standalone biometric privacy statute in 2008: the Illinois Biometric Information Privacy Act (“BIPA”). Today, BIPA is more relevant than ever and should act as a statutory blueprint for states looking to protect personal privacy and biometric data amid a global pandemic. Ultimately, though, BIPA must be supplemented by federal legislation drafted in its likeness to effectively protect individuals’ privacy on a national level.
II. Background of the Biometric Information Privacy Act
To fully understand BIPA and all its implications, one must appreciate the context in which it was enacted. The Illinois legislature passed BIPA in October 2008. The Act was passed in the immediate wake of the bankruptcy of Pay By Touch, a company which operated the largest fingerprint scan system in Illinois. Pay By Touch’s pilot program was used in grocery stores and gas stations, and its bankruptcy left users unsure of what would become of their biometric data – i.e., their fingerprints. “Biometric data – a person’s unique biological traits embodied in not only fingerprints but also voice prints, retinal scans, and facial geometry – is the most sensitive data belonging to an individual.”
Understandably, private citizens in Illinois and across the country want to safeguard their sensitive biometric data. With potential issues such as identity theft and data manipulation more prevalent than ever, people have plenty of incentives to ensure their unique identifiers stay private. In response to those concerns, legislatures have passed statutes to address biometric data and personal privacy. BIPA represents one of the most stringent of such acts in the country, setting strict requirements for the management of biometric identifiers in Illinois.
BIPA defines “biometric identifier” as (1) a retina or iris scan, (2) fingerprint, (3) voiceprint, or (4) a scan of hand or face geometry. Further, “biometric information” refers to any information, regardless of how it is captured, converted, stored, or shared, based on an individual’s biometric identifier used to identify an individual. The requirements outlined in Section 15 of the Act – which addresses the retention, collection, disclosure, and destruction of biometric data – implicate a slew of potential legal issues. The section stipulates that a private entity can collect a person’s biometric data only if it first informs the subject that a biometric identifier is being collected, informs them of the specific purpose and length of term it is being collected for, and receives a written release from the subject.
Further, the Act outlines the following concerning retention of such data:
(a) A private entity in possession of biometric identifiers or biometric information must develop a written policy, made available to the public, establishing a retention schedule and guidelines for permanently destroying biometric identifiers and biometric information when the initial purpose for collecting or obtaining such identifiers or information has been satisfied or within 3 years of the individual’s last interaction with the private entity, whichever comes first.
Thus, BIPA represents a statute narrowly aimed at maintaining the security of biometric data. While BIPA was relatively unknown in Illinois between 2008-2015, a wave of litigation has since swept through the state as employees began suing their employers. Such litigation was seemingly inevitable, as BIPA provides sweeping protection for individuals against biometric data abuse. The complexities of such issues have become clearer and potential legislative solutions to them even more important in the midst of a global pandemic.
III. Personal Privacy & Biometric Data in the COVID-19 Pandemic
The issues surrounding data privacy have become increasingly relevant in the ongoing COVID-19 pandemic, which effectively digitized the workplace as we know it. As the pandemic raged in the early months of 2020, workplaces around the globe were suddenly forced to digitally migrate to an online work environment. An inevitable result of newfound online worksites has been an increase in the utilization of biometric data. In an effort to facilitate remote work, companies have had to make work-related information accessible online. Employment attorney Eliana Theodorou outlines the ensuing issues for companies undertaking such efforts in an article entitled “COVID-19 and the Illinois Biometric Information Privacy Act.” For example, Theodorou writes, “Some of these platforms involve video recording or access by fingerprint, face scan, or retina or iris scan, which may result in the capture and storage of sensitive biometric information.” Thus, the collection and retention of biometric data has necessarily increased during the pandemic as companies made information accessible remotely when they shifted online.
Potential privacy issues accompanying the storage of biometric data will become even more difficult to navigate as companies return to physical workplaces with the pandemic still raging. Per Theodorou, “As workplaces reopen, there will likely be an uptick in the collection of biometric data as employers turn to symptom screening technologies that collect biometric data.” This could include, for instance, contactless thermometers and facial recognition scanning technologies used for contactless security access. The issue will thus continue to be the collection and storage of sensitive biometric data as employers return to work with the newfound priorities of social distancing and limited contact. The reality is that biometric data is still a relatively new concept, with its own specific set of issues and potential solutions. Personal privacy becomes ever harder to maintain in a digital world, with the use of biometric information often a necessity both for remote access and in-person return to work. Ultimately, the risks associated with the collection of biometric data remain largely undefined or misunderstood by employers. That lack of understanding has been exacerbated by a global pandemic necessitating a digital work migration.
IV. Possible Solutions to the Privacy Issues Raised by COVID-19 and Remote Workplaces
Illinois has provided a stellar blueprint for biometric data privacy in BIPA. However, other states have been slow to follow. As of November 2021, only a handful of other states have enacted legislation aimed at the protection of biometric data. Texas and Washington, like Illinois, have passed broad biometric privacy laws. Other states like Arizona and New York have adopted more tailored biometric privacy approaches, while others have enacted laws specifically aimed at facial recognition technology. There are also proposed bills awaiting legislative approval in many more states. Ultimately, implementing widespread legislation on a state-by-state basis will be a slow and drawn-out process, rendering countless Americans’ biometric data vulnerable. Rather than continue this state-based campaign to solidify biometric data privacy, citizens must turn to the federal government for a more comprehensive and consistent solution.
The primary roadblock to legitimate privacy in the biometric information space is the lack of a centralized federal initiative to address it. “Despite its value and sensitivity, the federal government currently has no comprehensive laws in place to protect the biometric data of U.S. citizens.” The privacy issues inherent in the popularization of biometric data in pandemic-era remote workplaces demand federal attention. A wide-ranging statute applicable in all states is the first step in properly addressing these issues. Congress should look to BIPA as a blueprint, for it remains the only state law passed to address biometric data privacy which includes a personal call to action. It is unique in that regard, especially considering it was passed in 2008, and consequently provides the most aggressive statutory response thus far to potential privacy concerns. Whether a federal act is feasible remains unclear. In August 2020, Senators Jeff Merkley and Bernie Sanders introduced the National Biometric Information Privacy Act of 2020, which suggests the imposition of nationwide requirements similar to those outlined in BIPA. The viability of such an Act is doubtful, as previous privacy legislation has been difficult to pass. However, it is a sign of movement in the right direction – toward increased protection of personal privacy in a pandemic which has made biometric data more relevant and potentially at-risk for improper management and manipulation.
Luke Shadley is a third-year law student at Northwestern Pritzker School of Law.
The development of AI systems has reached a point at which these systems can create and invent new products and processes just as humans can. There are several features of these AI systems that allow them to create and invent. For example, the AI systems imitate intelligent human behavior, as they can perceive data from outside and decide which actions to take to maximize their probability of success in achieving certain goals. The AI systems can also evolve and change based on new data and thus may produce results that the programmers or operators of the systems did not expect in their initial plans. They have created inventions in different industries, including the drug, design, aerospace, and electric engineering industries. NASA’s AI software has designed a new satellite antenna, and Koza’s AI system has designed new circuits. Those inventions would be entitled to patent protection if developed by humans. However, the United States Patent and Trademark Office (USPTO) has refused to assign the patent rights of these inventions to the AI systems.
The USTPO Denies Patent Rights to AI Systems
In a patent application that listed an AI system, DABUS, as the inventor, the USPTO refused to assign the patent right to DABUS and thus denied the patent application. DABUS invented an emergency warning light and a food container. The USPTO based its decision mainly upon a plain reading of the relevant statutes. 35 U.S.C § 115(a) states that “[a]n application for patent that is filed … shall include, or be amended to include, the name of the inventor for any invention claimed in the invention.” 35 U.S.C § 100(a) defines an “inventor” as “the individual, or if a joint invention, the individuals collectively who invented or discovered the subject matter of the invention.” 35 U.S.C § 115 consistently refers to inventors as natural persons, as it uses pronouns specific to natural persons, “himself” and “herself.” 35 U.S.C § 115 further states that the inventor must be a person who can execute an oath or declaration. The USPTO thus refused to extend its interpretation of “inventor” to an AI system, and it has stated that “interpreting ‘inventor’ broadly to encompass machines would contradict the plain reading of the patent statutes that refer to persons and individuals.
The Federal Circuit follows the same approach. In Beech Aircraft Corp. v. EDO Corp., the Federal Circuit held that “only natural persons can be ‘inventors.’” Therefore, in the current U.S. legal system, patent rights cannot be assigned for AI-generated inventions even though such inventions would be entitled to patent protection had they been created by humans.
Decisions regarding the patent protection for AI-generated inventions have spurred some disputes among academics. The creator of DABUS, Stephen Thaler, insisted that the inventions created by DABUS should be entitled to patent protection because DABUS is a system that can devise and develop new ideas, unlike some traditional AI systems that can only follow fixed plans. Stephen Thaler contends that DABUS has not been trained using data that is relevant to the invention it produced. Therefore, he claims, that DABUS independently recognized the novelty and usefulness of its instant inventions, entitling its invention patent protection. Thaler also raises an argument regarding the moral rights of inventions. Although current U.S. patent law may recognize Thaler as the inventor of these inventions, he emphasizes that recognizing him rather than DABUS as the inventor devalues the traditional human inventorship by crediting a human with work that they did not invent.
Some legal academics support the contentions of Stephen Thaler. For example, Professor Ryan Abbott agrees that AI systems should be recognized as inventors and points out that if in the future, using AI becomes the prime method of invention, the whole IP system will lose its effectiveness.
However, there are also objections to Thaler’s contentions. For example, AI policy analyst Hodan Omaar disagrees that AI systems should be granted inventor status because she believes that the patent system is for protecting an inventor’s economic rights, not their moral rights. She points out that the primary goal of patent law is to promote innovations, but Thaler’s proposed changes to patent law do little to do so. She argues that the value of protecting new inventions is for a patent owner rather than an inventor, which means that it makes no difference who creates the value. Thus, she concludes that listing DABUS as inventor makes no difference to the patent system. Omaar further argues that the proposed changes would introduce a legally unpunishable inventor that threatens human inventors, because the government cannot effectively hold AI systems, unlike individuals or corporations, directly accountable if they illegally infringe on the IP rights of others.
Patent Rights to AI Systems in Other Jurisdictions and Insights on U.S. Patent Law
Some foreign jurisdictions take the same stance as the United States. The UK Court of Appeal recently refused to grant patent protection to the inventions generated by DABUS because the Court held that patent law in the UK requires an inventor to be a natural person.
Despite failing to in the US and UK, Thaler succeeded in getting patent protections for the inventions created by DABUS in some other jurisdictions that allowed listing DABUS as the inventor. South Africa granted patent protection to a food container invention created by DABUS. This is the first patent for an AI-generated invention that names an AI system as the inventor. The decision may be partially explained by the recent policy landscape of South Africa, as its government wants to solve the country’s socio-economic issues by increasing innovation.
Thaler gained another success in Australia. While the decision in South Africa was made by a patent authority, the decision in Australia is the first decision of this type made by a court. The Commissioner of Patents in Australia rejected the patent application by Thaler, but the Federal Court of Australia then answered the key legal questions in favor of permitting AI inventors. Unlike patent law in the US, the Australian Patents Act does not define the term “inventor.” The Commissioner of Patents contended that the term “inventor” in the Act only refers to a natural person. However, Thaler successfully argued to the Court that the ordinary meaning of “inventor” is not limited to humans. The Court noted that there is no specific aspect of patent law in Australia that does not permit non-human inventors.
Examining the different decisions regarding the patent application of DABUS in different jurisdictions, we can see that the different outcomes may result from different policy landscapes and different patent law provisions in different jurisdictions.
For example, South Africa has a policy landscape where it wants to increase innovation to solve its socio-economic issues, while in the U.S., the government may not have the same policy goals related to patent law. Australia’s patent law does not limit an “inventor” to mean a natural person, while U.S. patent law specifically defines the word “inventor” to exclude non-human inventors in this definition. Thus, it is reasonable for U.S. patent law not to grant patent rights to AI-systems for AI-generated inventions, unless the legislature takes actions to broaden the definition of “inventor” to include non-human inventors.
The primary goal of the U.S. patent law is to promote innovation. If those who want to persuade the U.S. legislature to amend the current patent law to allow non-human inventors cannot demonstrate that such a change is in line with that primary goal, then it is unlikely that the legislature would support such a change. Whether granting patents to AI systems and allowing those systems to be inventors can promote innovation is likely to be an ongoing debate among academics.
Jason Chen is a third-year law student at Northwestern Pritzker School of Law.
